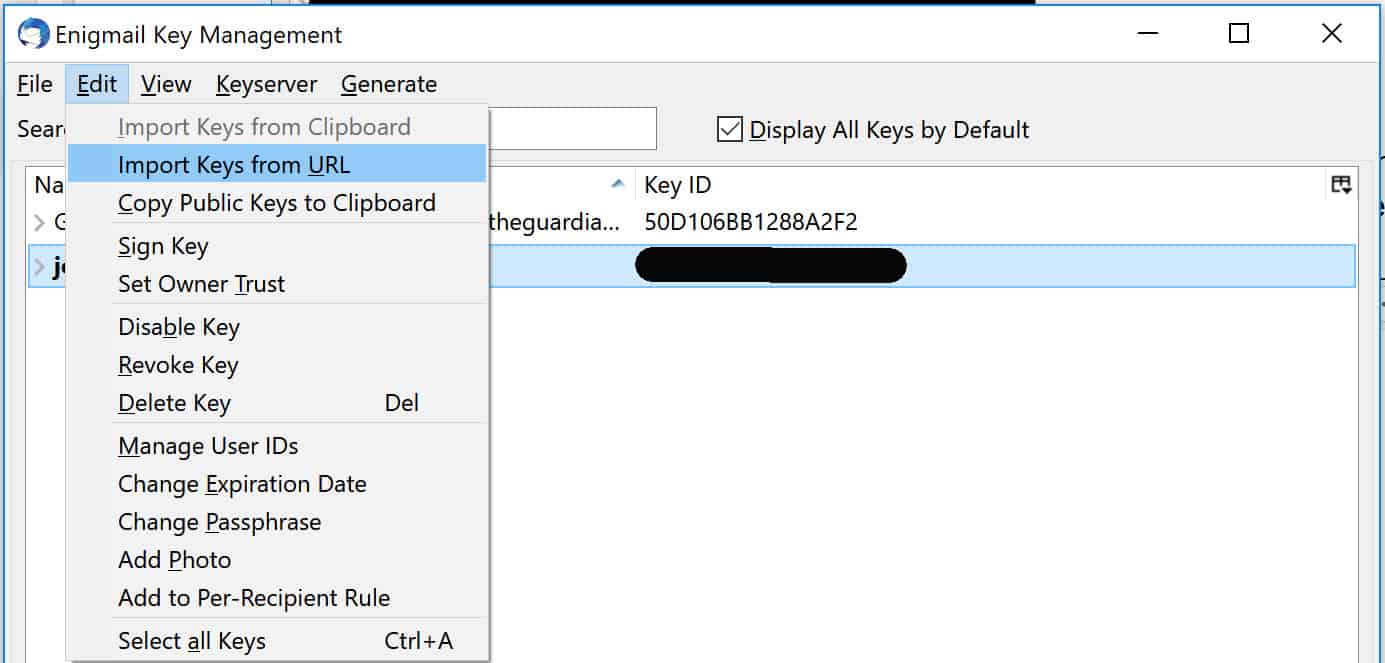
Peerless Tips About How To Get A Pgp Key
To get started doing this, hover over the “my cabinet” tab in the top menu bar area, then select “account settings”.
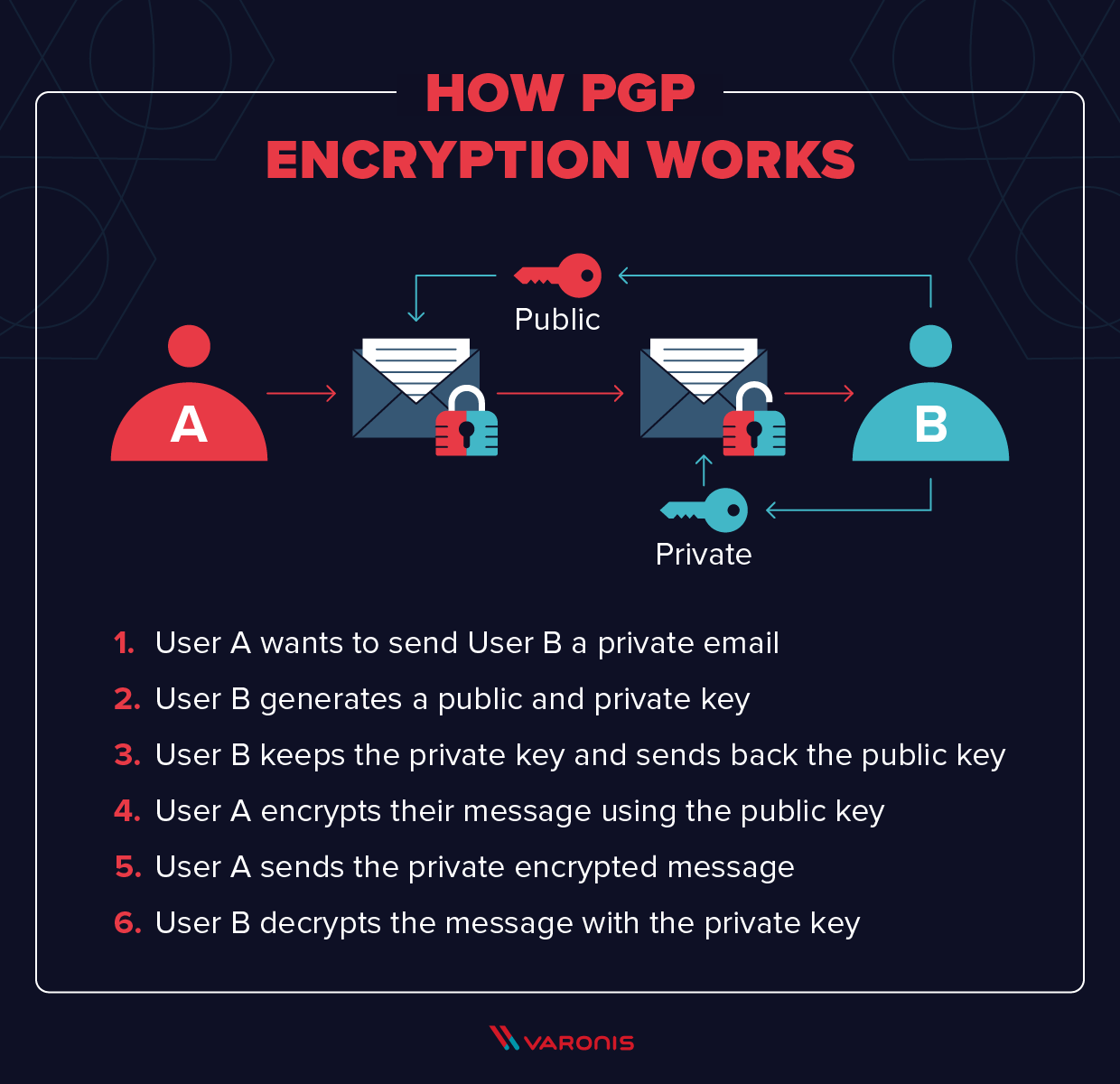
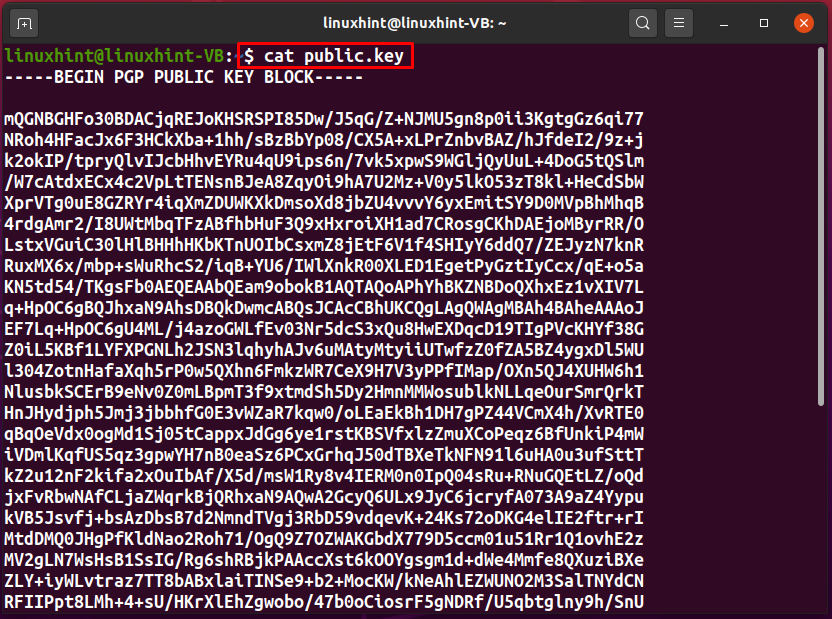
How to get a pgp key. Pgp uses key ids to refer to public keys for a variety of purposes. License pgp command line 10.1.0. These are not, properly speaking, fingerprints, since their short length prevents them from being able to securely.
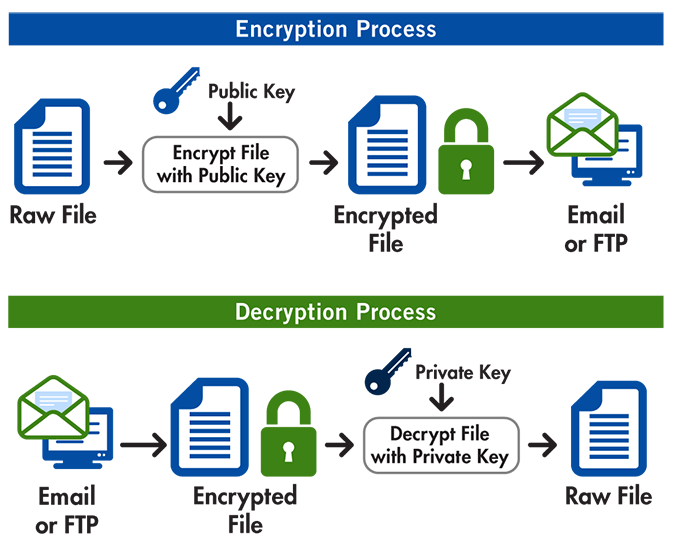
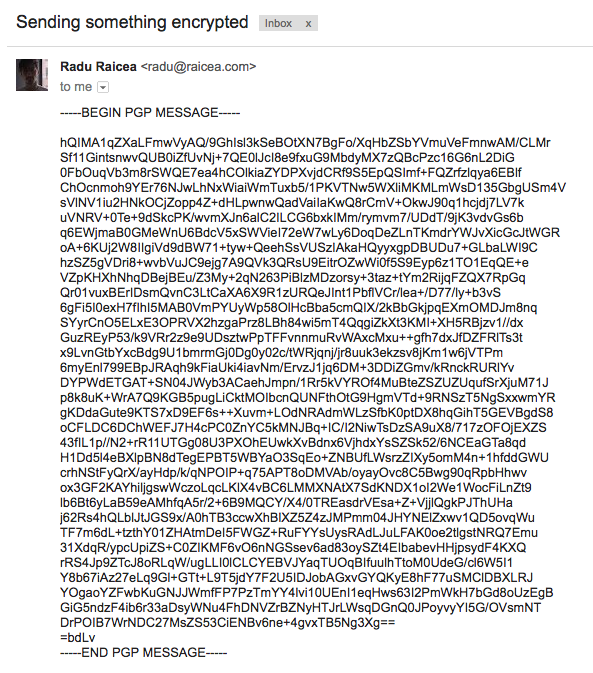
The private key is not visible like the public one, but you can get it following these instructions: Decrypt a message using a pgp private key. To create a key pair using pgp command line follow these steps:
The three steps needed to use pgp keys are: Id_rsa.pub the main thing is the.pub which means it’s probably a public key. If you will be generating a pgp key on a token,.
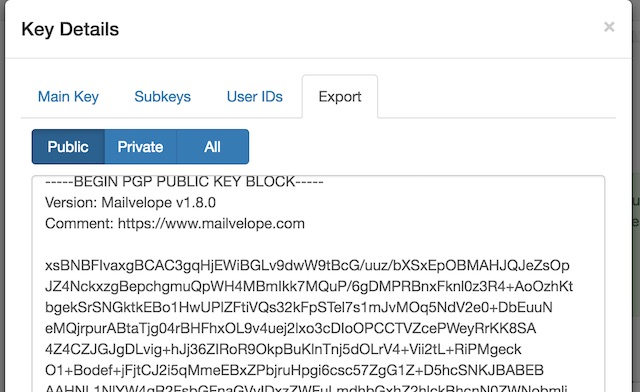
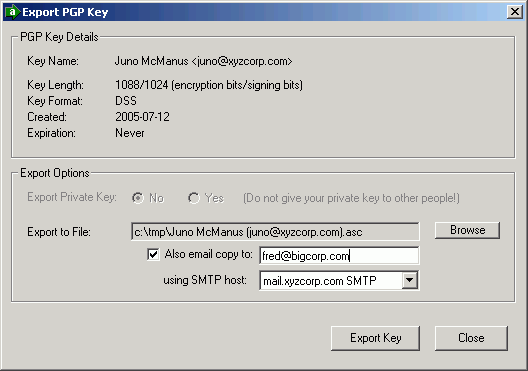
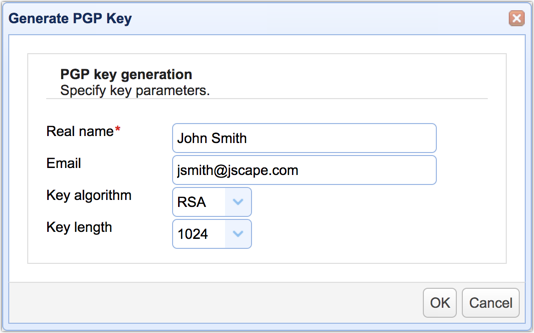
Asc file that includes the public key. If the answer is “yes” then they need to send you the key. For this example we will be creating a personal openpgp key pair.
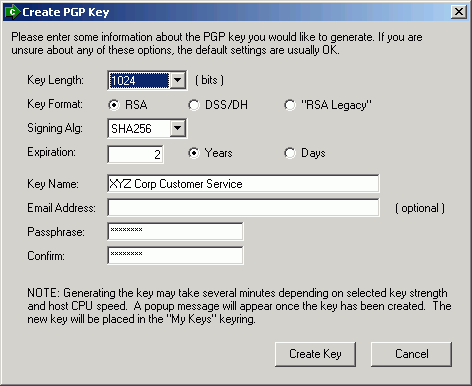
Navigate to file > new key pair and then choose the key format you want to create. Navigate to the pgp keys tab and then click the generate button. For versions of pgp command line 10.1 and.
The goal is to get the public key fingerprint using a separate channel. On the command line, enter: Ecc is still not widely supported in many pgp client applications so we advise that.